Azure Private DNS Resolver and Azure Point to Site VPN
You might access resources such as Azure SQL databases or Azure Storage accounts if you're connecting to a Microsoft Azure network externally (from a non-Azure VM or VPN); mainly if you operate Cloud-only services and don't have an external DNS provider, such as Active Directory - connecting to private link resources, you may have to edit your local host's file and override local DNS to point to the IP of the private endpoint for each service.
This is not sustainable, not scalable, and you might end up throwing your hands in the air and switching back to public-facing services and just whitelisting other users' Public IPs to gain access to Azure resources - which can lead to its own set of issues, such as unmanaged IPs left with access to resources after contractors or users leave or have finished their work, IP address changes if not managed correctly can allow any user or company to have a direct line of sight to your company resources.
Overview
Today we will concentrate on DNS resolution of Private Endpoints, using Azure DNS Private Resolver as a DNS proxy when connecting to Azure using a Point to Site VPN.
For this article, I assume you have an Azure Point to Site already set up; if you don't, you can refer to a previous article I wrote for Creating an Azure Point to Site VPN using Microsoft Entra ID authentication.
Disclaimer: Azure Private DNS Resolver is still in Public Preview at the time of this article (02/09/2022). If you aim to use this in a Production scenario, functionality and services may change. This also means there are current regional restrictions, and Azure Private DNS Resolver is not currently available in all regions. Also bear in mind the cost of this service.
So what is Azure DNS Resolver?
Azure DNS private resolver is a cloud-native, highly available, and DevOps-friendly service. It provides a simple, zero-maintenance, reliable, and secure Domain Name System (DNS) service to resolve and conditionally forward DNS queries from a virtual network, on-premises, and to other target DNS servers without the need to create and manage a custom DNS solution. Resolve DNS names hosted in Azure Private DNS Zones from on-premises networks as well as DNS queries for your own domain names. This will make your DNS infrastructure work privately and seamlessly across on-premises networks and enable key hybrid networking scenarios.
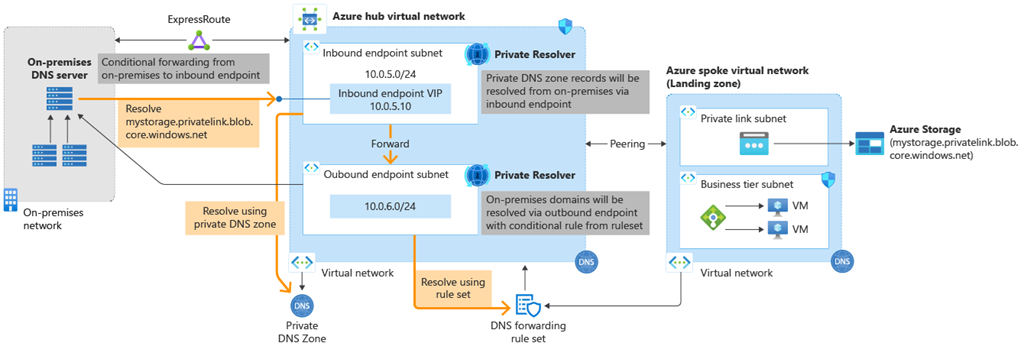
Customers will no longer need to provision IaaS-based solutions on their virtual networks to resolve names registered on Azure Private DNS Zones and can do conditional forwarding of domains back to on-premises, across multi-cloud providers, and public DNS servers.
This solution can work with your Azure ExpressRoute, Azure VPN, or Azure Bastion setup.
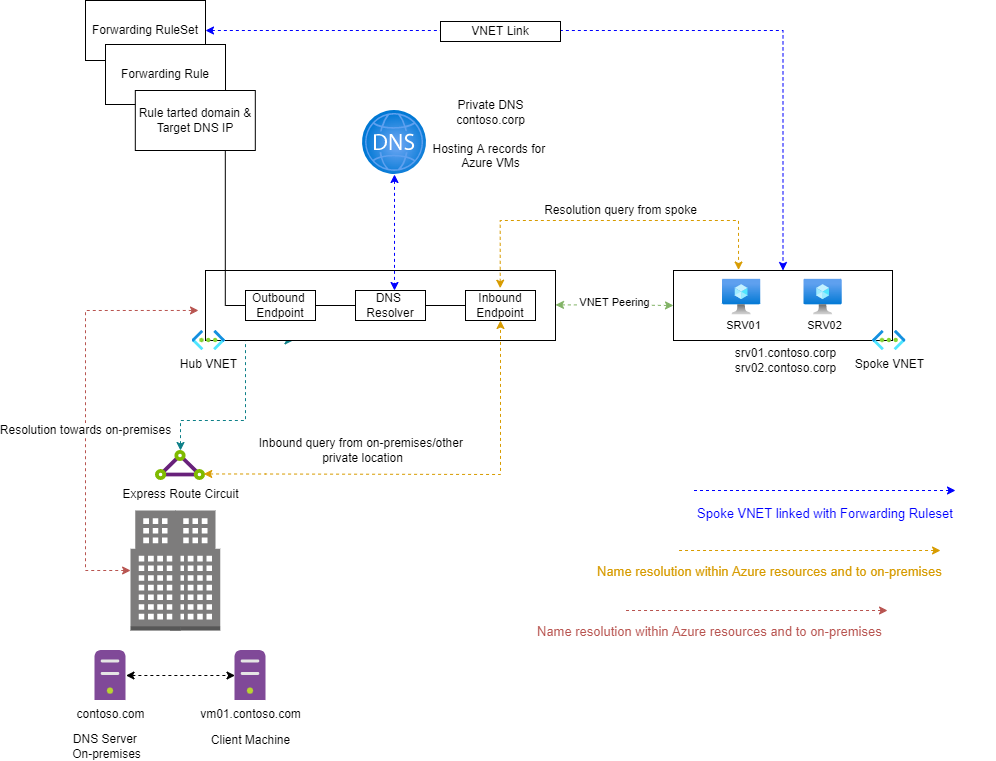
Inbound or Outbound?
Name resolution queries for Azure workloads from the on-premises network are conditionally forwarded to the Azure DNS private resolver inbound endpoint, which enables you to perform name resolution of workloads registered on Azure Private DNS Zones from on-premises.
| Endpoint | Blurb |
|---|---|
| Inbound Endpoint | Azure DNS private resolver inbound endpoint that receives the name resolution request from Azure & on-premises network and resolve names. |
| Outbound Endpoint | Azure DNS private resolver outbound endpoint conditionally forwards the request to on-premises or other target DNS servers. |
The Azure DNS private resolver inbound endpoint has a private IP that is part of a subnet where the endpoint has been created. The IP address of the DNS private resolver inbound endpoint is then set as a DNS server on the on-premises network.
Azure DNS private resolver outbound endpoint conditionally forwards the request to on-premises or other target DNS servers.
Today, we will connect to private endpoints to concentrate on the Inbound functionality of Azure Private DNS Resolver.
Deployment
To deploy Azure Private DNS Resolver, we will need a few things.
- A Virtual Network
- A subnet dedicated to resolving DNS queries (/28)
- A private endpoint (i.e. Storage Account, SQL Database) is linked to the virtual network.
Deploy DNS Private Resolver
I assume you already have a Virtual Network tied to your Virtual Network gateway as part of the 'Point to Site VPN' setup.
- Open the Azure Portal
- Click on + Create a resource
- Type in: DNS Private Resolver
- Click Create
- Select your Subscription
- Select your Resource Group (I recommend placing the DNS Private Resolver in the same resource group as your Virtual Network - but place this service in a Resource Group that makes sense for your environment, i.e. shared services or a specific network team resource group)
- Type in a name for your DNS Private Resolver (this is a regional service, but the name does not need a globally unique )
- Select your region (this needs to be the same region as the Virtual Network)
- Select your Virtual Network (the same Virtual Network that has your Virtual Network Gateway for the Point to Site VPN and your Private endpoints)
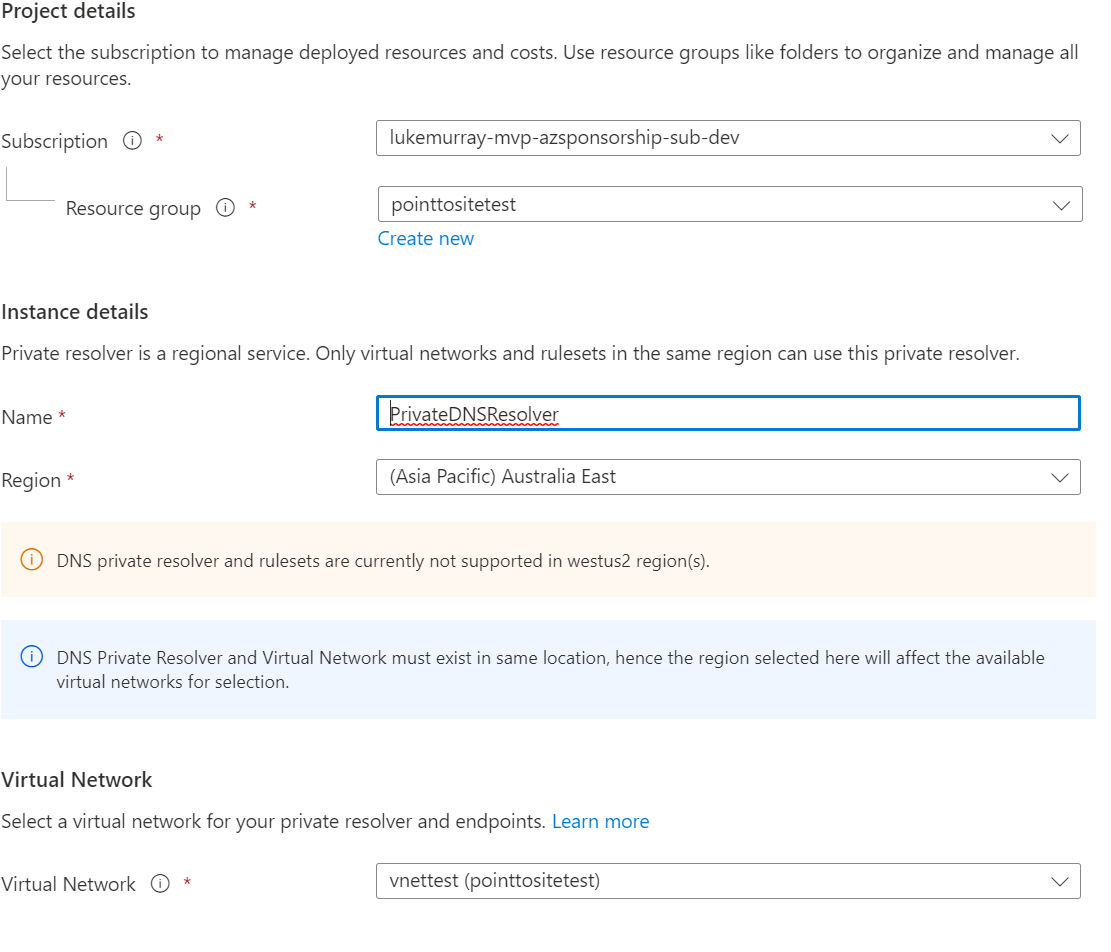
- Click Next: Inbound Endpoints >
- Now its time to add our Inbound Endpoint and create the Private DNS Resolver Subnet, click + Add an endpoint
- Type in your endpoint name (for example, InboundEndpoint)
- If you have already created a subnet, select it - else, click Create New
- Enter in your subnet name and address range
- Click Save
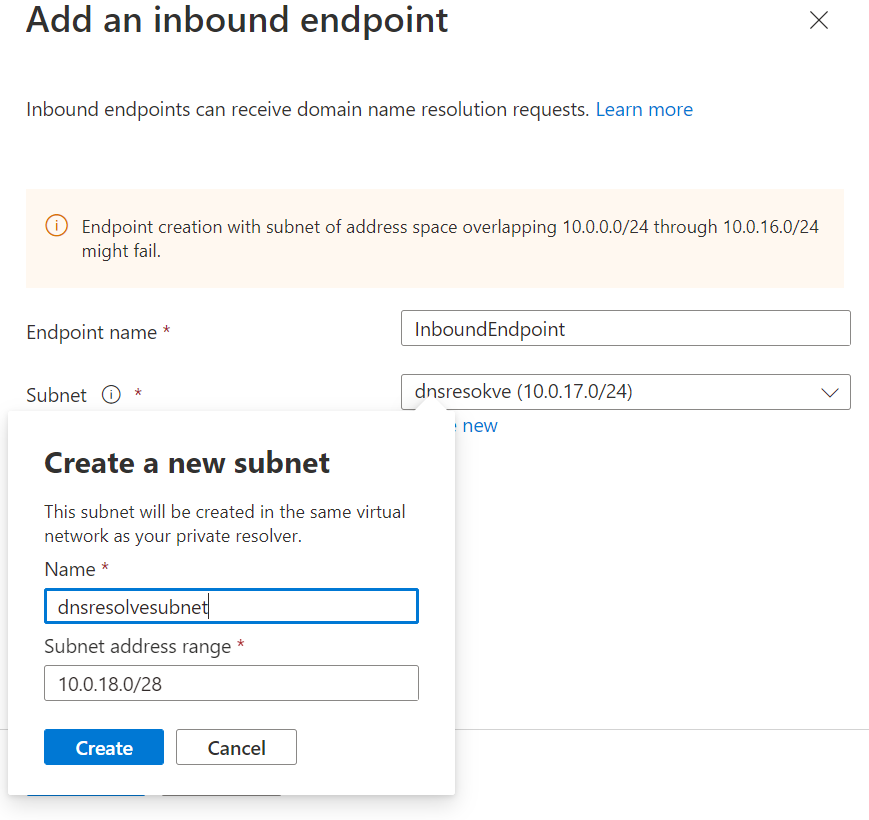
- Click Review + Create
- Click Create
Adjust Point to Site DNS
Now that the DNS Resolver has been created, with an inbound endpoint, allowing the lookup of private endpoints, we need to add the Private Resolver DNS relay to our point-to-site VPN configuration; first, we need the newly created private IP of the inbound endpoint.
-
Navigate to the DNS Private Resolver in the Azure Portal
-
Open your DNS Private Resolver service
-
Click on Inbound Endpoints
-
Make a note of the private IP of your inbound endpoint.
-
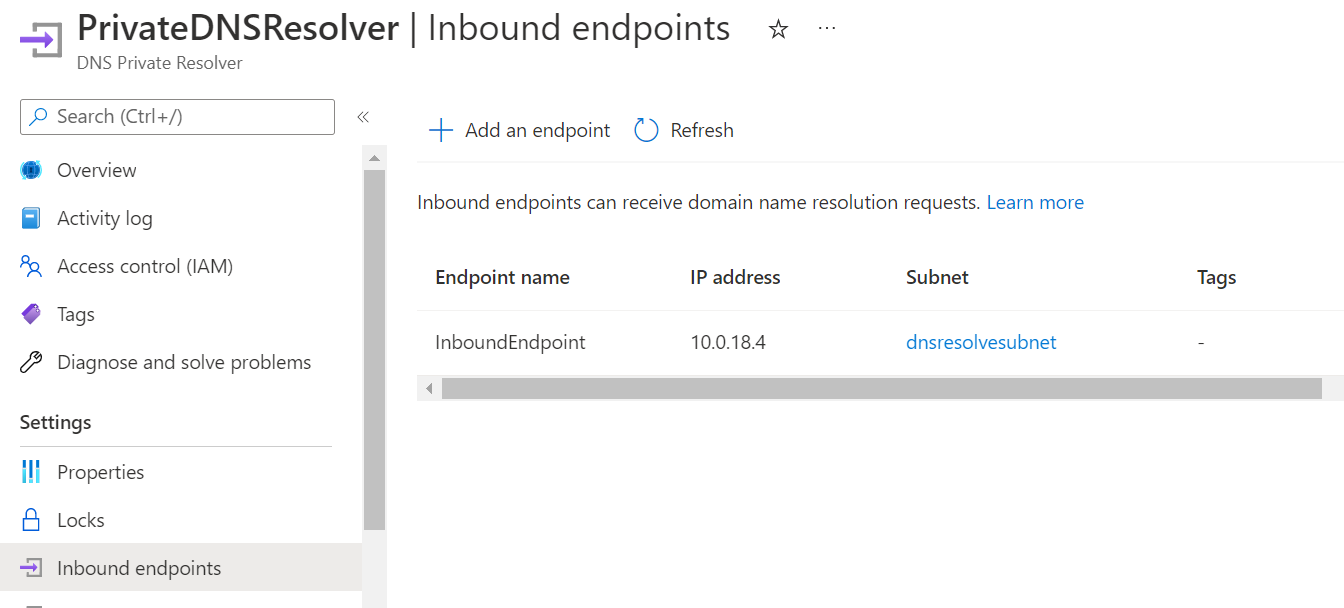
-
Now that the Private Inbound resolver has been configured, we need to add the DNS relay into our Azure VPN configuration so that our DNS queries will respond with a private endpoint; you will need to modify the 'azurevpnconfig.xml' file and reimport the VPN.
-
Right-click 'azurevpnconfig.xml' and edit in Notepad or Visual Studio Code
-
Under:
-
Add (replace the IP listed below with the IP of your Inbound endpoint copied earlier):
<clientconfig>
<dnsservers>
<dnsserver>10.0.18.4</dnsserver>
</dnsservers>
</clientconfig> -
Save and reimport to the Azure VPN Client
-
Once connected, ping a resource behind a private endpoint, and you should get the private IP of that resource back and should be able to connect to that resource privately.
-
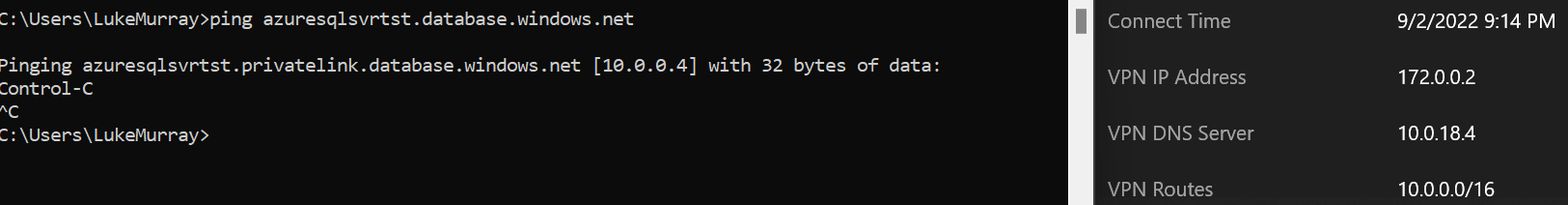
Any future or current private endpoints linked to the same Virtual Network will instantly be accessible without additional changes on the Azure VPN client. If you have a Hub & Spoke topology, then you may place the DNS Private Resolver in the HUB, then use forwarding rules to link to other peered VNETs.
Additional resources
The third-party resources below include reading and learning about the Azure Private DNS Resolver.
-
Quickstart: Create an Azure private DNS Resolver using the Azure portal
-
My Azure Private DNS Resolver Bicep export for reference:
param dnsResolvers_PrivateDNSResolver_name string = 'PrivateDNSResolver'
param virtualNetworks_vnettest_externalid string = '/subscriptions/57627713-eff2-44fa-a546-a2c8fde3c6e3/resourceGroups/pointtositetest/providers/Microsoft.Network/virtualNetworks/vnettest'
resource dnsResolvers_PrivateDNSResolver_name_resource 'Microsoft.Network/dnsResolvers@2020-04-01-preview' = {
name: dnsResolvers_PrivateDNSResolver_name
location: 'australiaeast'
properties: {
virtualNetwork: {
id: virtualNetworks_vnettest_externalid
}
}
}
resource dnsResolvers_PrivateDNSResolver_name_InboundEndpoint 'Microsoft.Network/dnsResolvers/inboundEndpoints@2020-04-01-preview' = {
parent: dnsResolvers_PrivateDNSResolver_name_resource
name: 'InboundEndpoint'
location: 'australiaeast'
}
]
}
}
