Start VM on Connect for Azure Virtual Desktop
One of the models of Cloud governance and cost in Microsoft Azure is 'Pay As You Go', ie. Pay for what you need when you need it.
The Azure Resource Manager fabrics allow you to scale up and down resources when you need it, whether built-in to the Azure portal or through various other automation mechanisms.
For Azure Virtual Desktop, this means ensuring that session hosts (Virtual Machines) are available for users to connect to consume their services when they need it the most, whether first thing in the morning or late hours of the evening.
One of the technologies that can help with this is: Start VM on Connect(Start VM on Connect allows users to start the virtual machine from a deallocated state).
You no longer need to create a Custom Role for Start VM on Connect - a built-in role now exists named: Desktop Virtualization Power On Contributor - once that role is assigned to the Azure Virtual Desktop application, you can skip straight to Configure
- Imagine a 9 AM -> 5 PM Monday to Friday business; during the day, Azure Virtual Desktop is available, however anything out of these hours (through Scheduled Shutdowns or Azure Automation Runbooks etc.), the session hosts are shut down to reduce operational costs.
- A business user gets some urgent work on Saturday morning and then tries to connect to Azure Virtual Desktop resources to complete the work; because they were turned off outside of business hours, they can't connect and then have to ring IT support to get resources started (the alternative would be to leave Virtual Machines running, which may or may not be needed).
- Using 'Start Virtual Machine on Connect', the moment that the user attempts to connect a Virtual Machine is started.
- Then it allows the users to log in and do their work without a call to IT, overall saving money, as the hosts are only started when they are first needed. The feature will also only turn on additional VMs (if available) when the first VM reaches the session limit.
This is a host-level setting, so setting 'Start VM on Connect' will affect all session hosts in the host pool. Therefore, you cannot target specific Virtual Machines in a session host at this stage. This is now supported for both Personal and Pooled session hosts!
As of 03/07/21 (NZ date format - DD/MM/YY): The Start VM on Connect feature is currently in public preview. This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Follow the guide below to implement; the Microsoft documentation is pretty good but hoping this might fill in a few gaps for people.
Create a Custom Role for "Windows Virtual Desktop"
For the "Windows Virtual Desktop" service principal (this should already exist, it is an inbuilt SPN created by the Azure infrastructure, it is currently called Windows Virtual Desktop but expect this name to be updated in the future) to have the ability to Start a Virtual Machine, we first need to give it rights. You could give it Contributor or Virtual Machine Contributor rights but want to go with the least privileged to create a custom role.
- Log in to the Azure Portal
- Navigate to the Subscription (you can only currently create custom roles at a subscription level) that your session hosts exist in
- Look for the Subscription ID (copy this, we will need it later on, usually found on the Overview window of the Subscription)
- Download the AVD-StartVMOnConnect JSON file below and save it to a location you can edit.
{
"properties": {
"roleName": "AVD-StartVMOnConnect",
"description": "Custom role, designed to allow 'Windows/Azure Virtual Desktop' rights to Start session hosts.",
"assignableScopes": [
"/subscriptions/<SubscriptionID>"
],
"permissions": [
{
"actions": [
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
-
Open up the JSON file (this is the Custom Role we are creating, as you can see, we are only allowing the ability to Read a Virtual Machine and Start it)
-
Replace the:
with your subscription ID, created earlier and save the JSON file. -
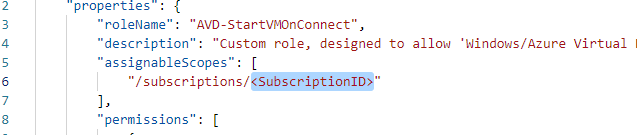 .
. -
Click on Access Control (IAM) on the left-hand side blade
-
Click Add
-
Click Add Custom Role
-
-
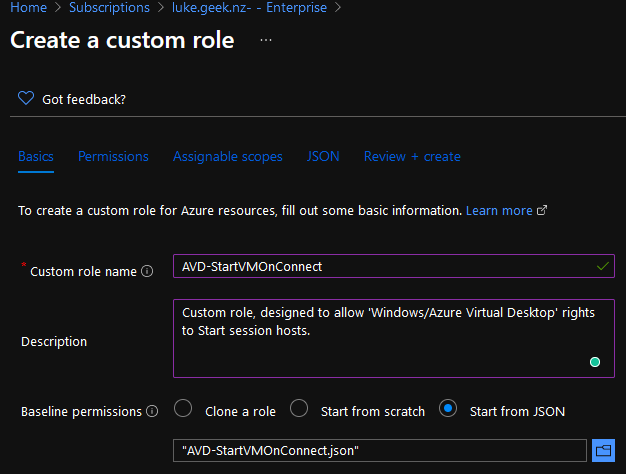
Name your Custom Role Name something meaningful, for example, AVD-StartVMOnConnect.
-
Add a meaningful Description; for example, mine is:
Created: 03/07/21
Created by: Luke Murray
Created for: Custom role, designed to allow 'Windows/Azure Virtual Desktop' rights to Start session hosts.
-
For: Baseline permissions, select Start from JSON
Select the JSON file you downloaded and edited earlier
-
-
Click on Next
-
Verify the permissions are as below (if they aren't, you may need the redownload or check the JSON file for syntax issues - I recommend downloading Visual Studio Code):
-
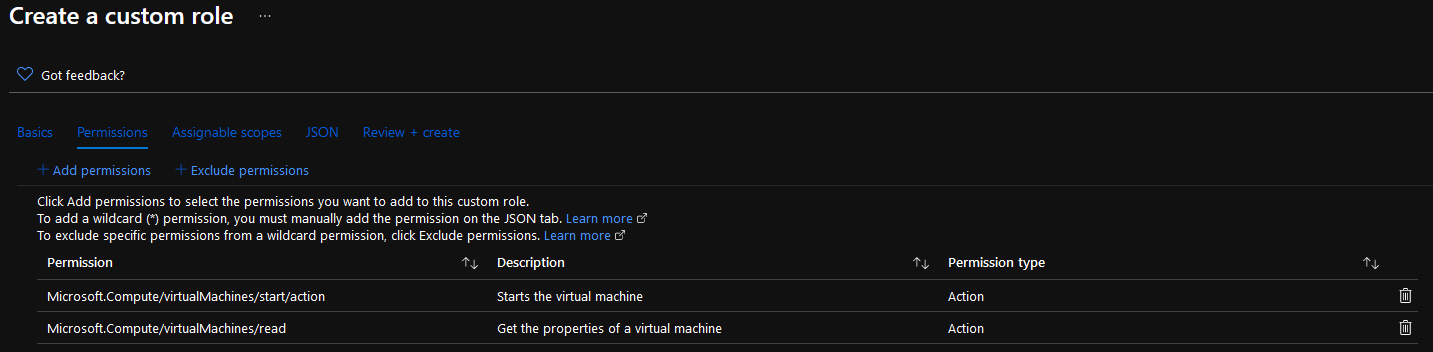
-
Click Next
-
We used the subscription property to select the assignable scope (i.e. the scope is where this role will be available for you to assign access to), but now using the Azure Portal, we can select a specific Resource Group to limit the roles access, please be careful with doing this, especially if you are planning on expanding out your Azure Virtual Desktop infrastructure in the future as you may forget that this role may not be available in other resource groups. I am going to leave mine at the Subscription level and click Next
-
Here we can verify and save the changed JSON file (if you want for future reference) and click Next to review your configuration.
-
Click Create to create your Custom Role!
-
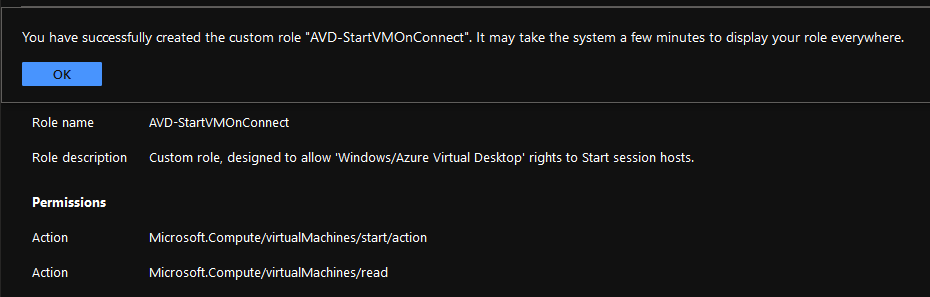
Assign your Custom Role
Now that you have created your custom role for Azure Virtual Desktop, it is now time to assign it, and this is where you can assign and lock down the role; in my case, I only have one Resource Group where my session hosts sit in, so going to assign it a Resource Group level, but feel free to assign this at a subscription level.
- Log in to the Azure Portal
- Navigate to the Resource Group (or Subscription) that has your Azure Virtual Desktop session hosts
- Click on Access Control (IAM) in the left-hand side blade
- Click on + Add
- Click on Add role assignment
- Select the Role you created earlier (i.e. AVD-StartVMOnConnect)
- Specify the 'Windows Virtual Desktop' service principal and select Save
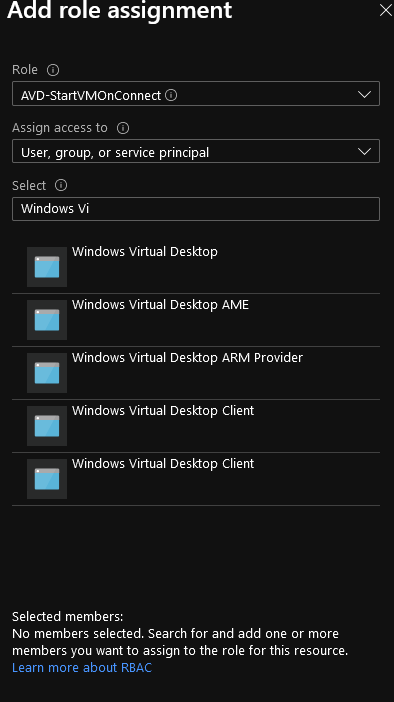
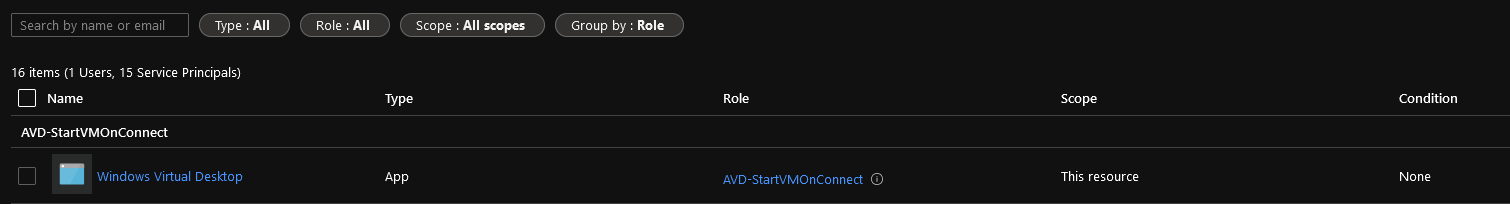
- If you want, you can click on Role Assignments to verify your role has been assigned:
Configure Start VM on Connect
- Log in to the Azure Portal
- Navigate to your Host Pool
- Click on Properties
- Select 'Yes' to Start VM on Connect
- Click Save
- Congratulations, you have now set up Azure Virtual Desktop - Start VM on Connect; next time someone connects to a turned-off Azure Virtual Desktop session host, the Virtual Machines will now automatically start the users will get a prompt like below:
- Before finally prompting for their login credentials!
